How Email Spam Bots Work and How to Stop Them
Understanding how email spam bots work and how to avoid them
Imagine opening your inbox to find it flooded with hundreds of unsolicited emails—phishing attempts, fake offers, and fraudulent schemes—mixed among your important messages. If this sounds familiar, you’re not alone. Nearly half of all email traffic worldwide is spam, costing businesses billions in lost productivity and security breaches every year. The impact of email spam extends beyond mere inconvenience; it undermines user trust, overwhelms communication channels, and exposes individuals and organizations to cyber threats.
At the center of this problem are email spam bots. An email spam bot is an automated program designed to flood inboxes with unwanted messages. Spammers employ these bots to deliver everything from advertisements to sophisticated phishing scams. But what drives these spammers? Why invest in creating these bots?
For many, it starts with the simple goal of testing whether an email address is valid, ensuring a steady flow of targets. Others employ spam for more malicious purposes, like phishing, where they trick recipients into divulging sensitive information or gaining unauthorized access to corporate networks. There’s also the aim of denial of service, where massive waves of spam are sent to disrupt communication by overwhelming inboxes. Then there are traditional scams—fraudulent schemes aiming for financial gain, whether by promoting fake products or luring people into costly traps.
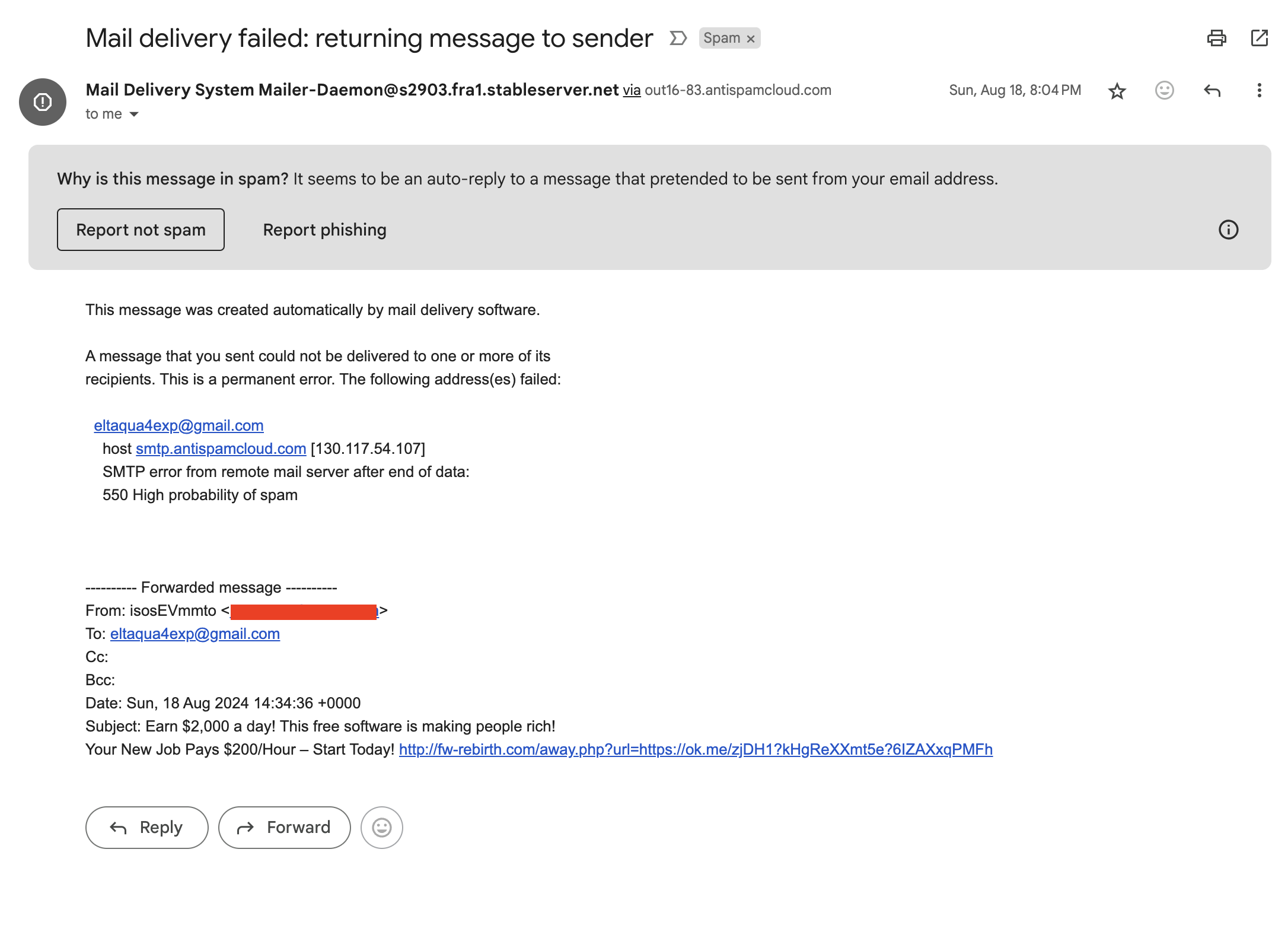
An email spammer trying to trick you into believing you were trying to send them the spam email, just to avoid getting tagged as “spam”
In this article, you’ll learn how an email spam bot works, how it evades detection, and what you can do to protect yourself and your digital assets from its relentless assault. From understanding the anatomy of these bots to building effective defenses using tools like Formspree, we’ll cover everything you need to know to stay one step ahead of the spammers.
How Email Spam Bots Work
An email spam bot often functions as part of a broader network known as a botnet. These botnets, controlled by spammers or cybercriminals, consist of thousands or even millions of compromised devices, from computers to IoT gadgets. Each bot in this network plays a small but critical role in executing the spammer’s larger strategy: overwhelming inboxes, testing email functionality, or distributing malicious content. The coordinated actions of these botnets enable spammers to send massive volumes of spam emails simultaneously, often making them harder to trace and block.
Target Acquisition
The first step in any spam campaign is acquiring a list of target email addresses. Spam bots are programmed to crawl the web continuously, scraping email addresses from publicly available sources such as websites, forums, social media profiles, and directories.
They also obtain addresses through more illicit means, like purchasing them from data breaches or hacking into databases. Even websites that post their contact email address for legitimate reasons can inadvertently become easy targets for these bots. (To protect against this, using a form service like Formspree can help site owners collect user messages without exposing their email addresses directly.)
Crafting the Spam Message
Once they have a list of targets, spammers need to craft messages that maximize engagement or accomplish their intended goal, whether it’s phishing or spreading malware. Modern spam bots use sophisticated techniques to create emails that appear legitimate, often spoofing trusted senders or mimicking recognizable brands. They might dynamically generate content, mixing generic messages with personalized information scraped from social media or other online sources, increasing the likelihood that the email will evade spam filters and trick the recipient into engaging.
Delivery and Evasion
The final step is the delivery method. Spam bots automate the email-sending process, often using compromised servers or devices to distribute messages in bulk. To evade detection, they employ various tactics like rotating IP addresses, using legitimate-looking domains, and crafting messages that bypass common spam filters. Some bots might even use snowshoe spamming, a technique that distributes spam across many IP addresses to avoid triggering filters. By constantly adapting to anti-spam defenses, these bots maintain their ability to infiltrate inboxes and carry out their malicious activities effectively.
Beyond the Inbox: Spam in Different Forms
Email isn’t the only place where spam bots wreak havoc. On social media platforms, spam bots take on different personas, creating fake accounts to flood comment sections, send unsolicited messages, or artificially inflate likes and followers. These bots can spread misinformation, promote scams, and manipulate public opinion, all while evading detection through rapid account creation and deletion.
Comment spam bots target websites and blogs, posting irrelevant or promotional content in comment sections. Their goal? To insert malicious links, manipulate SEO rankings, or simply clutter the site with junk. These bots operate much like any email spam bot but with the added aim of driving traffic to specific websites, often under false pretenses.
Then there are form spam bots, which exploit online forms—like contact pages or surveys—by making automated submissions. These submissions might include fake contact requests, irrelevant messages, or harmful links. The intent is often to flood databases with junk data or to exploit website vulnerabilities for further attacks.
Here’s a quick look at how form spam bots can affect a simple “contact me” form:
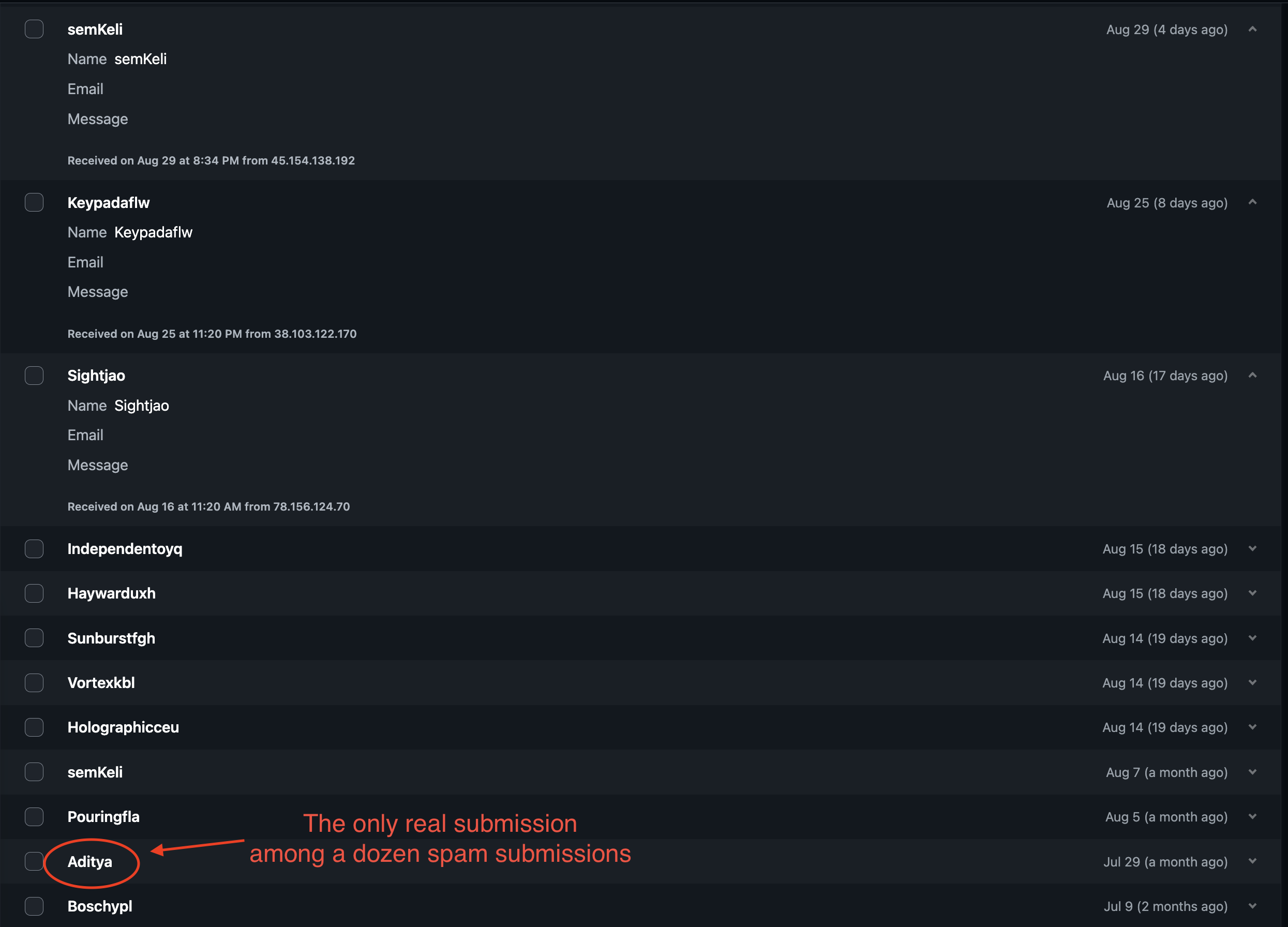
While the tactics differ, the malicious intent remains the same: disrupt, deceive, and manipulate. Understanding these diverse forms of spam helps us recognize patterns and deploy more secure defenses across all digital fronts.
Understand Spam Types
Spam messages come in many flavors, each with distinct characteristics and purposes, making it crucial for users to recognize and handle them appropriately. Here’s a look at some of the common types of spam:
- Phishing Spam: Perhaps the most dangerous, these emails mimic legitimate companies or contacts to steal sensitive information. They often contain links that lead to fake websites where unsuspecting users are tricked into entering personal data.
- Commercial Spam: These messages are typically unsolicited advertisements. While sometimes merely annoying, they can also include misleading or fraudulent offers designed to trick recipients into making unwise purchases.
- Malware Spam: This type involves emails that contain or link to malicious software. They are designed to infect the recipient’s device, allowing the spammer to steal data, take control of the device, or use it to send further spam.
- Scam Spam: Often seen in the form of lottery scams, inheritance scams, and too-good-to-be-true business deals, these spams promise significant financial gain in return for a small fee or confidential information.
- Image Spam: Employing images instead of text to evade spam filters, such a junk email often advertises pharmaceuticals, weight loss programs, or stocks. The image itself can contain misleading information or links to dubious websites.
- Chain Mail Spam: These messages urge recipients to forward the email to multiple contacts. Often based on superstitions or fake warnings, they primarily waste time and bandwidth.
- Spammy Offers: Similar to commercial spam, these emails offer free trials, amazing deals, or gifts to lure users into providing personal information or making a purchase.
- Fake Ads: These emails promote counterfeit goods ranging from high-end watches to medications, often at dramatically low prices to attract buyers.
- Political or Ideological Spam: Used to spread propaganda or disinformation, these messages target specific groups to influence opinions or create discord.
Each type of spam has markers that can help users identify them: generic greetings, urgency claims, unexpected attachments, or links that seem out of character for the supposed sender. Recognizing these signs can help users decide the appropriate actions—delete, report, or simply ignore—thus maintaining a safer communication environment. This awareness is important to defend against the strategies of spammers.
Spotting the Bots: Human vs. Machine
Identifying messages from spam bots can be crucial in maintaining online security. Here are several red flags that signal a potential bot rather than a human sender:
- Generic Greetings and Signatures: Emails that begin with vague salutations like “Dear user” or “Hello, friend” are often not personalized and could be sent by bots. Similarly, messages that end with generic or missing signatures may also indicate automation.
- Urgency Tactics: Bots frequently use urgent language to prompt quick actions. Phrases like “Immediate action required” or “Limited time offer” should raise suspicions, especially if the email comes from an unexpected source.
- Poor Grammar and Spelling: While not always a definitive indicator, frequent grammatical errors and misspelled words can suggest that the message was not crafted by a native speaker or a professional entity, but rather by a bot using imperfect algorithms.
- Repetitive Language: Messages that repeat phrases or seem unnaturally structured may be generated by simple bots designed to send bulk spam.
- Content Inconsistencies: If the content of the email doesn’t align with known information about the sender, or if there are mismatches in the sender’s name and email address, it’s likely a bot.
- Verification: Always verify suspicious links, attachments, and information. Do not click on anything that seems out of the ordinary without ensuring its legitimacy.
Building Your Anti-Spam Defense
Now that you know all the ways in which spam can exist, here are a few quick ways in which you can protect yourself from it:
- Keep Your Email Private: One of the simplest yet most effective ways to reduce spam is to keep your email address private. Instead of listing your contact email directly on your website or social media, consider using a form service like Formspree. This protects your email from being scraped by bots and keeps it out of the hands of spammers.
- Use Spam Filtering Services on Your Forms: For website owners, protecting online forms is crucial to avoid spam submissions that can flood your inbox and databases. Utilize spam filtering services such as Akismet, which are designed to detect and block spam before it reaches you. Implementing additional measures like honeypot fields and CAPTCHAs can further enhance security by distinguishing between human users and bots. Formspree has its own Formshield and supports Google’s reCAPTCHA as well as hCaptcha to help you filter out bots.
- Email Filtering Tools: Deploy spam filters that come with your email service and consider additional third-party tools for enhanced protection. Regularly update your filters and review their settings to ensure they are optimized to catch new types of spam. Training your email filter by marking missed spam can also improve its accuracy over time.
- Data Sharing Awareness: Be mindful of where and how you share your personal information online. Spammers often gather email addresses from publicly accessible sources. Avoid sharing your email openly and be cautious with whom you share sensitive information.
- Reporting Spam: Always report spam emails to your email provider. This not only helps remove the spam from your inbox but also contributes to the overall improvement of spam detection algorithms, helping others in the process.
Building Bot-Proof Forms with Formspree
Formspree offers a reliable way to create secure, bot-proof forms on websites. As a forms backend provider, Formspree focuses on protecting your forms from spam and bot interference, ensuring that the interactions and data you receive are genuine. It uses smart detection methods to differentiate between human users and automated scripts. This system analyzes submission patterns, helping to block spam bots effectively while minimizing disruption for real users.
Formspree employs effective detection methods to identify and block spam bots. These methods are designed to analyze submission behaviors and discern whether they originate from human users or automated scripts. This approach allows Formspree to maintain a high level of security while minimizing inconvenience for real users.
Setting up Formspree on your website is straightforward. Whether through embedding Formspree’s API or using simple HTML form actions, developers can easily implement secure and efficient forms. This setup not only keeps your forms safe from bots but also streamlines the form management process, allowing you to concentrate on user engagement rather than handling spam.
Do you receive a lot of junk email? How do you handle them? Let us know below!